Microcorruption 0x06 - Reykjavik
Prev: 0x05 Johannesburg
Next: 0x07 Whitehorse
The manual for this level tells us that it’s implemented some form of encryption, and sure enough there’s a new “enc” function which has a ton of instructions. First, let’s run through the program normally to see what happens.
The program asks us for a password as usual, but if we examine the Disassembly window we realize we can no longer view the instructions. And, if you were paying close attention to the opcodes at address 2400, you’ll notice that they are completely different from before the “enc” function!
At this point, it’s pretty clear what “enc” does: it steps through the opcodes at address 2400 and unencrypts them. This prevents the instructions from being printed in the original program disassembly, but fortunately does not prevent us from accessing them while the program is running.
Before:
After:
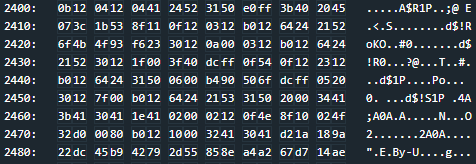
Set a breakpoint after the call to “enc” and check out address 2400. These are the unencrypted opcodes. Paste them into your favorite disassembler (you can try onlinedisassembler, or the disassembler provided by the site itself) and stop when you find a “ret” instruction, indicating the end of the function.
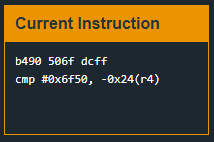
Just above the “ret” we find something interesting: “cmp 0x6f50, -0x24(r4).” If this comparison passes, 0x7f is pushed onto the stack, which is the interrupt code needed to unlock the door according to the lock manual. So, we need the value “506f” to be at address “-0x24(r4).” If we examine the Live Memory Dump window, we see that this instruction is at address 2448. Break there and continue, entering a dummy password when prompted.
When you hit the break, enter “read r4-24” to read what values are there. Surprise – it’s our password!
To solve the level, enter “506f” as the password.
Prev: 0x05 Johannesburg
Next: 0x07 Whitehorse
Next: 0x07 Whitehorse
The manual for this level tells us that it’s implemented some form of encryption, and sure enough there’s a new “enc” function which has a ton of instructions. First, let’s run through the program normally to see what happens.
The program asks us for a password as usual, but if we examine the Disassembly window we realize we can no longer view the instructions. And, if you were paying close attention to the opcodes at address 2400, you’ll notice that they are completely different from before the “enc” function!
At this point, it’s pretty clear what “enc” does: it steps through the opcodes at address 2400 and unencrypts them. This prevents the instructions from being printed in the original program disassembly, but fortunately does not prevent us from accessing them while the program is running.
Before:
After:
Set a breakpoint after the call to “enc” and check out address 2400. These are the unencrypted opcodes. Paste them into your favorite disassembler (you can try onlinedisassembler, or the disassembler provided by the site itself) and stop when you find a “ret” instruction, indicating the end of the function.
Just above the “ret” we find something interesting: “cmp 0x6f50, -0x24(r4).” If this comparison passes, 0x7f is pushed onto the stack, which is the interrupt code needed to unlock the door according to the lock manual. So, we need the value “506f” to be at address “-0x24(r4).” If we examine the Live Memory Dump window, we see that this instruction is at address 2448. Break there and continue, entering a dummy password when prompted.
When you hit the break, enter “read r4-24” to read what values are there. Surprise – it’s our password!
To solve the level, enter “506f” as the password.
Prev: 0x05 Johannesburg
Next: 0x07 Whitehorse